Lab 12-4 securing data with encryption – Embarking on Lab 12-4: Securing Data with Encryption, this exploration delves into the realm of data protection, unveiling the intricate mechanisms that safeguard sensitive information from unauthorized access. Encryption stands as a cornerstone of modern cybersecurity, and this lab provides a comprehensive understanding of its methods, algorithms, and best practices.
As we navigate the complexities of data encryption, we will unravel the intricacies of symmetric-key and asymmetric-key encryption, along with the indispensable role of hashing functions. We will examine the strengths and weaknesses of renowned encryption algorithms such as AES, DES, and RSA, empowering you to make informed decisions based on specific security requirements.
Data Encryption Methods

Data encryption is the process of converting data into a form that cannot be easily understood by unauthorized people. There are several different methods of data encryption, each with its own advantages and disadvantages.
Symmetric-Key Encryption
Symmetric-key encryption uses a single key to both encrypt and decrypt data. This makes it relatively fast and efficient, but it also means that the key must be kept secret. If the key is compromised, then the data can be decrypted.
Asymmetric-Key Encryption
Asymmetric-key encryption uses two keys: a public key and a private key. The public key is used to encrypt data, and the private key is used to decrypt it. This makes it more secure than symmetric-key encryption, because even if the public key is compromised, the data cannot be decrypted without the private key.
Hashing, Lab 12-4 securing data with encryption
Hashing is a one-way encryption method that is used to create a unique fingerprint of data. Hashes are often used to verify the integrity of data, or to store passwords in a secure way.
Encryption Algorithms
There are many different encryption algorithms available, each with its own strengths and weaknesses.
AES
AES (Advanced Encryption Standard) is a symmetric-key encryption algorithm that is used by the US government to protect classified information. AES is considered to be one of the most secure encryption algorithms available.
DES
DES (Data Encryption Standard) is a symmetric-key encryption algorithm that was developed in the 1970s. DES is no longer considered to be secure, and it has been replaced by AES.
RSA
RSA (Rivest-Shamir-Adleman) is an asymmetric-key encryption algorithm that is used to secure online transactions. RSA is considered to be one of the most secure encryption algorithms available.
Key Management
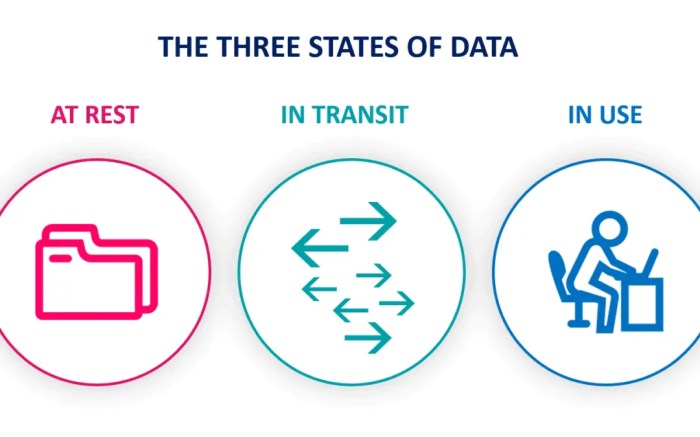
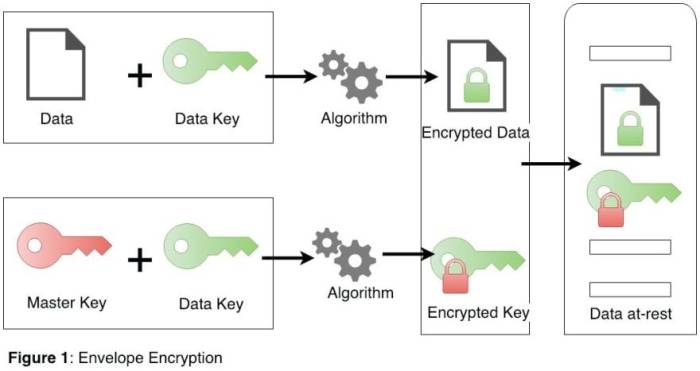
Key management is the process of generating, storing, and distributing encryption keys. It is important to manage keys securely, because if a key is compromised, then the data that is encrypted with that key can be decrypted.
There are several different key management systems available. The best key management system for a particular organization will depend on the organization’s size, security needs, and budget.
Encryption in Practice
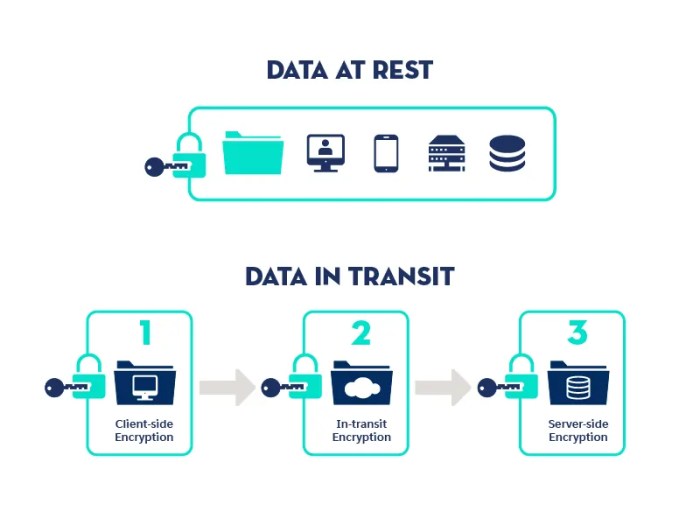
Encryption is used to secure data in a wide variety of applications, including:
- Online banking
- E-commerce
- Healthcare
- Government
Encryption can help to protect data from unauthorized access, theft, and modification.
Encryption Standards and Regulations
There are several different encryption standards and regulations that organizations must comply with. These standards and regulations include:
- HIPAA (Health Insurance Portability and Accountability Act)
- PCI DSS (Payment Card Industry Data Security Standard)
- GDPR (General Data Protection Regulation)
These standards and regulations specify the minimum requirements for encryption that organizations must meet.
Future of Encryption
The future of encryption is bright. There are several new encryption technologies that are being developed, including:
- Quantum computing
- Homomorphic encryption
These technologies have the potential to make encryption even more secure and efficient.
Query Resolution: Lab 12-4 Securing Data With Encryption
What is the difference between symmetric-key and asymmetric-key encryption?
Symmetric-key encryption uses the same key for both encryption and decryption, while asymmetric-key encryption uses different keys for encryption and decryption.
What is the role of a hash function in encryption?
A hash function is a mathematical function that converts data of any size into a fixed-size output, which is used to verify the integrity of data and detect unauthorized modifications.
What is the importance of key management in encryption?
Key management is crucial for ensuring the security of encrypted data, as it involves the generation, storage, and distribution of encryption keys in a secure and controlled manner.